![]()
In the previous articles we discussed the methods to crack passwords. We gave some practical numbers on how fast those attacks are and how to choose passwords of sufficient length. The key conclusion should have been that the length and the randomness is most important. It is more important than the use of a complicated character set (special characters).
An attacker will not spend 50000,- € on computing power if he could bribe an employee for 5000,- to open the safe.
Nevertheless, passwords are secrets which are ultimately associated with a person that cannot easily be excavated. Even extreme torture may not reveal the password. And it can be changed. All this is not true for e.g. fingerprints or iris scans – you should definitely watch the good old action movie “Demolition Man” from 1993 with Sylvester Stalone and Wesley Snipes.
Furthermore all types of secret-keeping soft- or hardware devices (certificates, token generators, mobile apps, ID cards,…) are by default not associated with a person at all. E.g. if a door is opened with a token card, this does not necessarily mean that the owner of the card opened the door or did enter the room. This holds true for all kinds of hardware devices as long as there is no feature that associates a specific person with the device. This is where passwords come into play again.
Just in case if you didn’t get the point right now: these article series is not just dedicated to IT professionals, it is important for everybody!
All kinds of secrets such as e.g. private keys and passwords shall be long enough, truly random, and unique. The latter means that they shall not be reused for different services or applications.
How many accounts, logins, passwords, PIN codes,… do you have? Count it, now!
Secrets are used everywhere today. Many web pages, social media, your mobile phone PIN, bank and credit card PINs and passwords, online banking, web shops, market places, online portals of your insurance companies, email accounts, your online music platforms, various Wifi networks, the public transport’s ticketing system, trading platforms, E-government platforms,…
Even for an outstanding genius it is impossible to remember so many long and random passwords.
The most simple solution to this problem is to use a password manager. It is a tool (or database) which is used to store passwords and other secrets. The password manager immediately resolves many problems. You do not have to remember all these passwords and PINs anymore. The password manager is doing it for you. And because of this you can
But what if an attacker finds this password database?
Yes, this is definitely an issue. It is like a treasury. Thus, good password managers secure the database with a password. Obviously, you cannot store this password within the password manager itself. You have to keep it ideally in your head. Choose this password wisely because it secures all other secrets you have. From now on this is your sole and most important password.
I suggest to use a list-of-words passwords using lowercase and uppercase letters at a length of about 20 digits (or more of course), or lowercase letters and numerals. Do NOT store it in a digital way neither on your computer, nor on your mobile or tablet! You could keep it handwritten1 in a sealed envelope and give it to somebody who you trust, e.g. one of your siblings or similar. Just in case if something bad happens to you. If you loose it all other passwords are lost and cannot be recovered under no circumstances. Except you used a weak password which can be recovered by a brute-force attack as has been discussed in the previous articles.
Password managers are around since decades but it seems that they are still just used by security professionals. So many people still don’t care about their passwords. Although it is just my subjective perception I believe that often these are the same kind of persons who say that they have nothing to hide but on the other hand these are exactly those whose Facebook accounts get regularly hacked…
During the past decades of software development many severe implementation mistakes have been made in respect to secure password storage. But we can assume that modern password managers are securely implemented.
So which password manager should I use?
The short answer is: „It does not matter. Any password manager is better than no one compared to having the same weak password everywhere.”.
Of course, a password manager is not a general problem solver. They even introduce new risks and attack vectors, e.g. that they are a single treasury of your passwords and that they depend on your “perfect” master password to stay secret. And if one tricks or tortures you, you immediately reveal all other passwords. But nevertheless, I am convinced that for a daily use it is still the better solution, independently if you use it professionally or personally. Of course there is further recommended reading, e.g. Stuart Schechter’s article “Before You Use a Password Manager” and experts might read Bruce Schneier’s article “On the Security of Password Managers”.
When using a password manager you need a really good password to secure all your treasures. But it is just a single one to remember.
A password manager is a piece of software which does the job of remembering passwords for you. Nowadays there are many different software packages available. All of them have different use-cases and, hence, different features and different pros and cons.
If you do not want to install and use any new software yet – for whatever reason – but you may want to smoothly get started with password managers then I’d suggest to start with the browser’s built-in password manager. Firefox, Chrome, Chromium, and probably most other browsers come with a ready-to-use password manger for web pages. In the following I’ll explain how to use Firefox’s password manager but it works similar on most browsers.
As already mentioned in the previous chapter, the most important issue of using a password manager is to have a single secure master password. This master password encrypts all other passwords stored within the password manager. That means that if you “loose” the password store, e.g. because your computer was hacked, your passwords are still secure as long as your master password is really strong.2
First of all we have to set this master password. Although the password manager could be used without master password you should be aware that this is definitely dangerous!
If you use the password manager without master password it does not encrypt your passwords on disk. That means if your computer gets somehow compromised the attacker can access all your secrets.
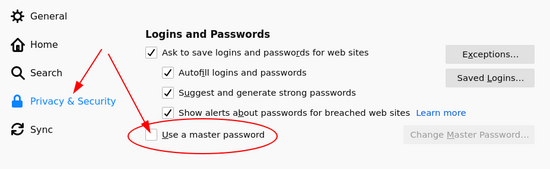
Open the menu and choose “Preferences”. A new Tab will open. On the left side select “Privacy & Security” and scroll down to “Logins and Passwords”. Check “Use a master password” and a new window will open. It requires you to set the master password. Choose it wisely!
If you are worried that you may forget it, write it down on a paper but do neither store it somewhere on the computer nor print it.
Once you set your master password try to login into one of your favorite web pages. Firefox will ask you immediately after login if it should save the password for you. The next time you try to login onto the same web page the browser will fill in username and password for you and to unlock the password database it will ask you to provide the master password. You don’t have to enter this password at every login because for your convenience it will store the master password in memory for some time.
Having this built-in password manager enabled you can – and should – change the passwords of your online services to real random and strong passwords and save it to the password manager.
In the Linux world it is pretty easy to generate passwords. There is e.g. the tool pwgen. If it isn’t already installed on your system just add it with the package manager (`apt-get install pwgen`). Once installed just type `pwgen 20 1` and it will output a random password with 20 digits.
But pwgen even exists for Windows. Head over to https://portableapps.com/apps/security/pwgen-portable and download and unpack it. Then just start it (double-click) and a window will open. Choose an appropriate password length and hit “Generate”.
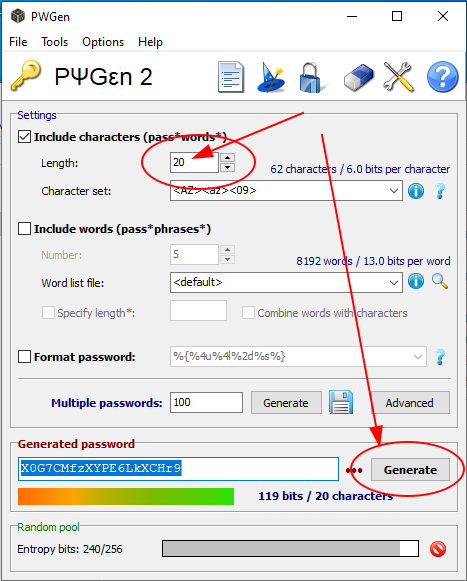
A new random password will immediately appear at the bottom. This password generator is a powerful tool. You can choose the character set. So if you wish you could add special characters (symbols) as well but as should have become clear from the previous articles the length of the password is more important than the size of the character set.
This password generator tool also supports to generate list-of-words passwords. You may even select your own words list as a source for the alphabet.
In this article we discussed that passwords are a critical point of security. If done wrong it may compromise the security of a whole system but on the other hand if done right it is an unrecoverable piece of security.
It is vital to have unique passwords for every service one might use. That’s why I suggest to use a password manager and I introduced the built-in password manager of Firefox as a good starting point for novice users. Don’t forget to set a master password, otherwise it is probability less secure as without password manager!
For a password in order to fulfill its part as a secure element it has to be really random. I therefore suggest to use a password generator and I introduced the powerful tool pwgen. It is available for Linux, MacOS, and Windows.
The built-in password managers of the browsers’ are simple tools. What they cannot do is to use the password database on various systems in parallel or for several users in parallel.
I’ll introduce a high secure password manager for personal use for several systems and/or users in one of the next articles.

Bernhard R. Fischer started his career as a network engineer responsible for building up a national IP network and later developing and maintaining the major Internet services for this network such as DNS and Email. After his studies of business economics and information systems on the University of Vienna he became a researcher and teaching fellow on the University of Applied Sciences of St. Pölten in the fields of computer networks, operating systems, and IT security. Since 2017 he is employed as a senior security consultant at Antares-NetlogiX GmbH.
During his whole career Bernhard contributed to a lot of public projects and discussions, attended conferences as a speaker, and voluntarily supported numerous open source projects not just as an advocate but as software engineer and developer. He always placed emphasis on robustness and quality of software and systems. He painstakingly investigates the details of everything and he willingly passes his knowledge to everybody who is interested.
Some of his own public projects can be found on Github, some articles and opinions on his personal Tech & Society Blog, and on Twitter. Bernhard is also into sailboat sailing and runs his own professional web site and produces the technical podcast Schiff – Captain – Mannschaft which is about sailing, seamanship and sailboats.
[1] Do NOT print it with the computer!
[2] Even the NSA does not have arcane forces and can somehow magically open the password store. They are as well bound to the laws of physics.