![]()
Password security is an everlasting topic. It is discussed since tens of years and will continuously be discussed in the future. It is also a subject to steady change because the needs for security change and the power to break security changes as well. Thus, no everlasting answer about the perfect passwords exists.
This series of articles tries to give an answer for a practical real world use of passwords as of today, in the year 2020. It studies how password security evolves and what hackers really can do, what they do, and what they cannot do. During the articles we will show how to practically choose passwords and secure systems in general where passwords play a role. The latter is almost everywhere they case as soon as users are involved.
This article is written for everybody who is interested in password security, not just administrators and engineers ;)
What do passwords do? Passwords secure whatever data. This could be to unlock an encrypted document, to open some secure hardware token, or to open a secure web site – meaning to login. Passwords are a fundamental element of the security of a system and are at the same time pretty fragile. Although alternatives such as fingerprints, iris scans, or hardware tokens have been suggested many times, they still never come alone without password. Using several mechanisms is called multi-factor authentication and will be discussed in a later article.
An attacker always has several options to break into such a secure system. Basically, this is either to break the security mechanism itself or to find the secret password to unlock the security mechanism.
Breaking the security mechanism means e.g. breaking the cryptography or somehow break into a system by using whatever intrusion technique. However, this usually is very “loud” meaning it can be detected or could be traced back to some attacker.
Finding the secret is much more elegant and silent. And it may open not just a single door but even the safe with the most valuable treasures. This article is about the discrepancies of passwords and their security.
Unfortunately, there is no general answer to this question. A different question could give more options to give valid answers. This is “How to find a yet unknown password?”. Let’s first try to understand which options an attacker has to find a password.
Assume a login form on a web page such as Facebook, Amazon, Paypal, or whatever portal. An attacker could simply try out a list of passwords. The username is not really a secret since in many cases – for the sake of simplicity – it’s simply an email address.
The main limitations of this type of attack are the bandwidth and the server-side performance. Both make it pretty slow and hence takes a huge amount of time to try a reasonable long list of password candidates. Of course, this attack is not carried out by hand but with specialized scripts.
If we assume that a single password test takes just 100 milliseconds, which sounds pretty quick, we can test 36000 passwords per hour. As we will see later this is terribly slow. It’s like winning a lottery jackpot.
Furthermore, it is pretty easy to protect a server from such attacks and well maintained systems today implement such prevention techniques, often out-of-the-box.
The phishing attack does not directly attack the password. It tricks the user to enter his credentials into a fake web page. This is a powerful attack as long as you can convince a user to click on the malicious link and let him enter his username and password.
This works as follows. The attacker first copies the desired web page to his own web server. Basically this could be any web page even Facebook or any financial service’s page.
Second, the attacker registers a domain which looks pretty close to the original one, like lacebook.com, or paypa1.com, or similar.
Third, he tricks the user to click the page, e.g. by sending an email like “Please revisit our page to verify your password, click lacebook.com ”, or similar. This could be sent by email or Whatsapp or even be built-in into some nice fancy mobile app or any other click bait which probably shows some piece of naked skin ;) or whatever is appropriate in the context of the user.
The user follows the link and he will see the web page which looks exactly like the original. If he does not carefully check the URL he will not notice any difference and he will enter his credentials. The web page will store the user’s input to the attacker’s database and will silently redirect the user to the real web page.
Trust me, it works, we tested it!
Obviously, the password is stored somewhere in a database on the server-side. Otherwise the service (e.g. the web page) could never tell if a password is correct. It compares the password sent by the user with the one in the database.
But the passwords are not stored directly as plaintext. They are obscured typically with a so-called hash function. This is done for security reasons that somebody who can read the database, e.g. like an administrator or developer, still cannot read the passwords.
Hash functions are one-way functions, meaning they cannot be reversed. With such a function we can create a hash from a password but we cannot calculate a password from a hash. But we could try several passwords and observe if they yield a specific hash.
Plaintext Password: hackme!
Hashed Passwords: $6$HZ.bqG1bxEx4JSVK$/itKJH5tzwwRsBrE18sEf83YsZPMboA6fYmjh3NzOjUL6jA/rWe5jKRmPF9peMPJHcsltQrSTkZAuILuzH
And this is how an offline brute-force attack works. Let’s assume that the attacker got such a database dump containing password hashes. He can try to compute the hashes of a list of well-known passwords and match it with the database dump. Compared to the online brute-force attack this method is pretty powerful because the only limitation is the computing power of the attacker. There is no network or online service limiting it. This attack is by orders of magnitude faster than the online version of it as we will see later.
Many developers mistakenly think that their code and database is secure because they use some kind of hash function, it’s very often less secure as they think. The security highly depends on the choice of the hash function. Vigilant attackers may find hashes on various places in a network.
The basic technique is to choose a random password, hash it, and compare the result to the hash we “found” somewhere in the network. If they match we successfully recovered a password. If not, choose the next random and try again.
The question is where do we get these “random passwords” from?
There are two options. First, we use a world list. A world list is a list of well-known passwords and we try each of them. Second, we randomly generate passwords. This will be discussed in the next article.
Word lists are available for download on the Internet. They have been collected from real passwords that have been leaked during the last decades. It has often be seen in the past that even big companies, such as e.g. Adobe, AOL, Apple, and many more, did store the users’ passwords not in a hashed way but directly as plain text...and they’ve been pwned!
We have a word list which contains approx. 3 billion passwords. As an example, the first few entries in the list contain the following passwords (Is yours on the list?):
123456, password, 12345678, pussy, qwerty, qwertz, 696969, letmein, michael, fuckme, jennifer, batman, test, 1111, porn
We can feed this list into a specialized hardware and let it hash all passwords and compare it to the hashes that we “found” somewhere in the network. As of today, this specialized hardware isn’t so specialized anymore. Actually, it is done by graphics cards (GPU) which are found in all gaming computers today.
The time it takes depends on the type of hash value that is used. There is big variety of hash functions out there which means almost every system has its own hash function. That means that there are hash functions used by Microsoft in Windows, other hash function used in Wifi networks, others in Apple’s Iphone, and yet another hash function in a random online shop’s database.
But to give an idea about the speed here are some benchmarks. These values are measured with a single NVIDIA RTX2070 Super which is a recent GPU model of NVIDIA. It calculates about 500000 hashes per second for the PBKDF2-WPA algorithm which is used in wireless networks and it is a pretty strong – meaning brute-force-resistant – algorithm. For NTLM which is used by Microsoft Windows and is an extremely old and weak algorithm it computes approx. 4 million hashes per second.
And this in turn means that an attacker who sniffed the hash of your weak wireless password, while sitting in his car nearby, needs 1 hour and 40 minutes to check it against the list of 3 billion passwords. Let’s further assume it is not just a random hacker how is doing this just for fun but somebody who is willing to invest some money and buys 20 of these GPUs, he will need just 5 minutes.
The NTLM hash can be calculated even much faster. This whole word list from above is checked in 12 ½ minutes, hence, there is no need to buy even a second of such a GPU – just get a coffee and its finished when you’re back.
I’d like to mention that I would estimate the performance of the world’s most powerful supercomputer of today, Summit, to at least 25000 times the power of that single RTX 2070.
Random passwords are much more secure if they are really random. But what does randomness really mean?
Randomness is something that can mathematically be described very well in theory but unfortunately it is much harder to create randomness with a computer that you might think. Furthermore it is not easy to tell if something is random, i.e. if just a single password appears it cannot directly be said if it is random or how random it is. That means that all those fancy randomness-meters do just half of their job.
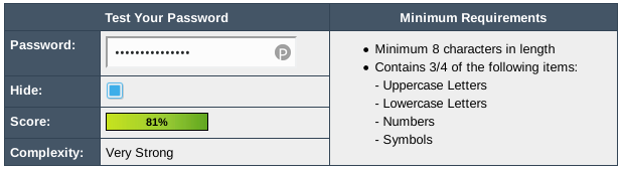
It’s even worse because humans are very bad at picking random passwords. Humans pick a “random” word in their sense which ends up being one of those in the 3 billion words list. And furthermore still, humans are worst at remembering random words. The brain is made for repetition but not uniqueness. That’s why humans stick to the same password all along.
Thus, security experts started to tell people to use a capital letter at the beginning or the end of the word or insert any special character at the end, such as a question mark or some punctuation symbol or similar.
Unfortunately this does not solve the problem because hackers know that as well. All it does is that it tricks the randomness-meter and suggests a false sense of security to the user. Because we – the attacker – can take this long word list and simply alternate it precisely in that way. We make the first letter a capital letter and try to append some special characters at the end. Let’s say there are 10 variations which means the list is 10 times as long. Now to find the correct password for an NTLM hash takes 10 times longer as well, i.e. 125 minutes. Let’s buy 4 additional GPUs, then we are down at 25 minutes again. Got it?

Bernhard Fischer (Antares Red Team)
(Bernhard Fischer)